
This is listed as as easy room (a very tricky easy room) and can be located here: https://tryhackme.com/room/madness
The goal here is to find two flags, one user and one root. No other questions.
First an nmap scan to see what we are working with.
┌─[✗]─[user@parrot]─[~]
└──╼ $sudo nmap -sV -O 10.10.225.104
[sudo] password for user:
Starting Nmap 7.92
( https://nmap.org ) at 2021-11-28 20:37 GMT
Nmap scan report for 10.10.225.104
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))Two ports 22 and 80. Since we don't have any clues about the ssh, I headed over to the website first.
I tried gobuster to enumerate different paths, but didn't find anything. One odd thing to note is the errored image at the top. Let's save and see what's going on.
┌─[user@parrot]─[~]
└──╼ $ wget http://10.10.225.104/thm.jpgTrying to open this file leads to error. Checking image header we see this is a PNG not a JPG as the filename indicates.
Using hexedit we can change this.
┌─[✗]─[user@parrot]─[~]
└──╼ $hexedit thm.jpg Change the first row:
00000000 FF D8 FF E0 00 10 4A 46 49 46 00 01Now open again and we have a secret link!

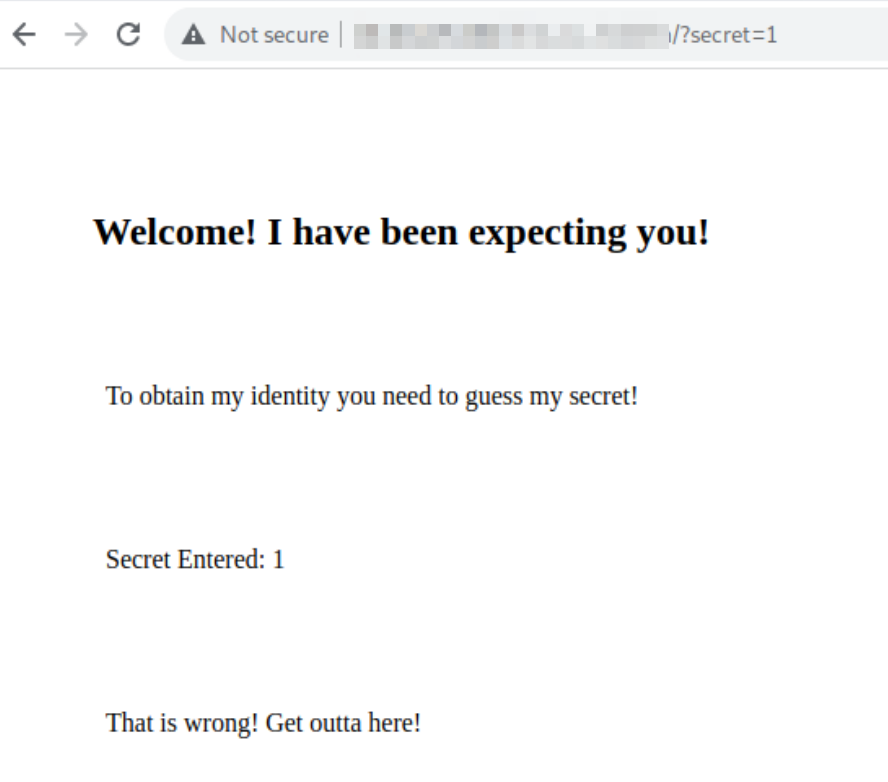
It looks like we can append the secret ID to the URL. We'll need to go through secrets 1-99. I used Burpsuite Intruder and created a number list with a python loop. Search through the results for a larger size and then navigate to the correct ID. Once there a secret phrase will be revealed. Save this for later.
At this point I was a little lost. It seemed everything had been accounted for, but we still had nothing. We had to manipulate the image to get it to open, maybe there is something else there.
Using steghide we can look for anything hidden in the image. This will require a password. Recall we have something that might work.
┌─[user@parrot]─[~]
└──╼ $steghide extract -sf thm.jpg
Enter passphrase:
wrote extracted data to "hidden.txt".Looking at the hidden.txt file we have yet another code of some sort. If not recognized (the hint gives this away) this is encoded using ROT13. head over to your favorite decoding site and decode this
And with that we have a username! But we still can't log in without a password. This next part I wouldn't have figured out and had to use google. The password is hidden in the rooms header image (which also appears at the top of this post).
Use the same process as we used on the other image. What is the password here? Might be nothing...only one way to find out.
Huzzah (sorry just finished watching the Great, excellent show by the way)! We now have a password!
Jump over to ssh and login with our new user and password. Simple enough, grab the first flag in the user's directory.
Now for the root flag.
I couldn't find anything in crontab or sudo permissions. Checking if anything has SUID set, we find a few things.
joker@ubuntu:~$ find /bin -perm -4000
/bin/fusermount
/bin/su
/bin/ping6
/bin/screen-4.5.0
/bin/screen-4.5.0.old
/bin/mount
/bin/ping
/bin/umount
joker@ubuntu:~$ sudo screenI went with the screen option as it seemed to stand out more. A quick search later and I had a python script we can run (located here: https://www.exploit-db.com/exploits/41154)
Make the script executable, then run it. You might encounter some errors, but don't worry, once done you'll be pleased to see the root prompt.
The last flag may or may not be hanging out in root's home directory.
That's it for this one. Thanks for reading and happy hacking!
-ott3r